CVE-2024-38856
Apache OFBiz Incorrect Authorization Vulnerability - [Actively Exploited]
Description
Incorrect Authorization vulnerability in Apache OFBiz. This issue affects Apache OFBiz: through 18.12.14. Users are recommended to upgrade to version 18.12.15, which fixes the issue. Unauthenticated endpoints could allow execution of screen rendering code of screens if some preconditions are met (such as when the screen definitions don't explicitly check user's permissions because they rely on the configuration of their endpoints).
INFO
Published Date :
Aug. 5, 2024, 9:15 a.m.
Last Modified :
Oct. 23, 2025, 2:49 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
Apache OFBiz contains an incorrect authorization vulnerability that could allow remote code execution via a Groovy payload in the context of the OFBiz user process by an unauthenticated attacker.
Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable.
Unknown
This vulnerability affects a common open-source component, third-party library, or a protocol used by different products. Please check with specific vendors for information on patching status. For more information, please see: https://lists.apache.org/thread/olxxjk6b13sl3wh9cmp0k2dscvp24l7w; https://nvd.nist.gov/vuln/detail/CVE-2024-38856
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | HIGH | 134c704f-9b21-4f2e-91b3-4a467353bcc0 |
Solution
- Upgrade to Apache OFBiz version 18.12.15 or later.
Public PoC/Exploit Available at Github
CVE-2024-38856 has a 52 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-38856.
| URL | Resource |
|---|---|
| https://issues.apache.org/jira/browse/OFBIZ-13128 | Issue Tracking |
| https://lists.apache.org/thread/olxxjk6b13sl3wh9cmp0k2dscvp24l7w | Mailing ListVendor Advisory |
| https://ofbiz.apache.org/download.html | Product |
| https://ofbiz.apache.org/security.html | Patch |
| http://www.openwall.com/lists/oss-security/2024/08/04/1 | Mailing List |
| https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-38856 | Third Party AdvisoryUS Government Resource |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-38856 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-38856
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
None
Target Acquired. The Ultimate Web Scanner & Auto-Exploitation Tool. From Recon to RCE in a single strike.
Python
Cybersecurity Toolkit
Go Java
CVE-2024-38856: Apache OFBiz remote code execution Scanner & Exploit
Python
CVE-2024-32113 & CVE-2024-38856
Python
备份的漏洞库,3月开始我们来维护
None
None
A Collection of scripts for CVEs Labs to build the lab automatically on your local machine
Shell Batchfile
A Collection of scripts for CVEs Labs to build the lab automatically on your local machine
Shell Batchfile
None
HTML
Links of research blogs published by me.
wy876
Python
wy876 POC | wy876的poc仓库已删库,该项目为其仓库镜像
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了1100多个poc/exp,长期更新。
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-38856 vulnerability anywhere in the article.

-
The Cyber Express
Top Cybersecurity Certifications to Boost Your Career in 2025
Cybersecurity professionals are the frontline warriors combating hackers, hacktivists, and ransomware groups. To fight with these cyber criminals, the world needs cybersecurity expertise who can acces ... Read more

-
Cybersecurity News
ESET’s Warning: Windows 10 Users Urged to Switch to 11 or Linux
With millions of German computers still running the soon-to-be-obsolete Windows 10, and a worryingly low adoption rate of Windows 11, ESET warns of a cybersecurity risk unless users take immediate act ... Read more

-
The Cyber Express
Critical Apache Vulnerabilities: Update Now to Avoid Major Risks
The Cyber Security Agency of Singapore has issued a warning about several critical vulnerabilities found in Apache software products. The Apache Software Foundation has rolled out security patches add ... Read more

-
The Cyber Express
Google Addresses Critical Baseband Flaws, Strengthens Pixel Defenses
Google recently addressed a flaw within cellular modem vulnerabilities that can pose risk to smartphone users. The cellular baseband is responsible for handling all cellular communications, including ... Read more
-
Cybersecurity News
Ajina.Banker: Unmasking the Android Malware Targeting Central Asian Banks
Screenshot of the sample found on the VirusTotal platformCybersecurity analysts at Group-IB have uncovered a sophisticated malware campaign targeting bank customers in Central Asia. Dubbed “Ajina.Bank ... Read more

-
TheCyberThrone
Apache OFBiz Vulnerability CVE-2024-45195 actively exploited
Apache OFBiz has got a security update for a flaw CVE-2024-45195 with a CVSS score of 7.5 that allows attackers to bypass authorization checks and execute arbitrary code on the server, even without v ... Read more
-
Cybersecurity News
Hackers target Apache OFBiz RCE flaw CVE-2024-45195 after PoC exploit released
Image: Rapid7According to a report from Imperva, over 25,000 malicious requests targeting 4,000 unique sites have been detected since the CVE-2024-45195 vulnerability in Apache OFBiz was disclosed. Th ... Read more

-
security.nl
Apache verhelpt kritieke RCE-kwetsbaarheid in ERP-oplossing OFBiz
Apache heeft een kritieke kwetsbaarheid in ERP-oplossing OFBiz verholpen waardoor een ongeauthenticeerde aanvaller op afstand code op het ERP-systeem kan uitvoeren. Onlangs werden twee andere beveilig ... Read more

-
The Cyber Express
Critical RCE Vulnerability Patched in Apache OFBiz (CVE-2024-45195)
Popular open-source enterprise Resource Planning (ERP) system, Apache OFBiz, recently discovered harboring a critical Remote Code Execution (RCE) vulnerability. Tracked as CVE-2024-45195, the Apache O ... Read more

-
Help Net Security
Apache OFBiz team patches critical RCE vulnerability (CVE-2024-45195)
For the fourth time in the last five months, Apache OFBiz users have been advised to upgrade their installations to fix a critical flaw (CVE-2024-45195) that could lead to unauthenticated remote code ... Read more

-
The Hacker News
Apache OFBiz Update Fixes High-Severity Flaw Leading to Remote Code Execution
Cybersecurity / Vulnerability A new security flaw has been addressed in the Apache OFBiz open-source enterprise resource planning (ERP) system that, if successfully exploited, could lead to unauthenti ... Read more

-
BleepingComputer
Apache fixes critical OFBiz remote code execution vulnerability
Apache has fixed a critical security vulnerability in its open-source OFBiz (Open For Business) software, which could allow attackers to execute arbitrary code on vulnerable Linux and Windows servers. ... Read more
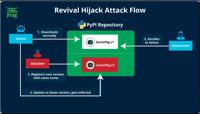
-
Cybersecurity News
Revival Hijack: A New PyPI Hijacking Technique Threatens Thousands of Packages
The JFrog security research team has uncovered a novel PyPI package hijacking method known as “Revival Hijack,” which has put over 22,000 packages at risk of exploitation. Unlike traditional typosquat ... Read more
-
Cybersecurity News
Publicly Exposed GenAI Development Services Raise Serious Security Concerns
Access to the API without the need for any authentication | Image: Legit SecurityA new report released by Legit Security has raised significant concerns about the security posture of publicly accessib ... Read more

-
Cybersecurity News
Proof-of-Concept Exploit Released for WhatsUp Gold Authentication Bypass (CVE-2024-6670)
Researcher Sina Kheirkhah of the Summoning Team has published the technical details and a proof-of-concept (PoC) exploit for a critical vulnerability, identified as CVE-2024-6670, affecting Progress S ... Read more

-
The Register
Check your IP cameras: There's a new Mirai botnet on the rise
in brief A series of IP cameras still used all over the world, despite being well past their end of life, have been exploited to create a new Mirai botnet. The vulnerability (CVSS 8.7, CVE-2024-7029) ... Read more

-
Dark Reading
Exploited: CISA Highlights Apache OFBiz Flaw After PoC Emerges
Source: tofino via Alamy Stock PhotoCISA has added a critical security flaw in the Apache OFBiz open source enterprise resource planning (ERP) system to its Known Exploited Vulnerabilities (KEV) catal ... Read more

-
security.nl
Apache OFBiz ERP-systemen opnieuw doelwit van aanvallen
Apache OFBiz ERP-systemen zijn opnieuw het doelwit van aanvallen, zo waarschuwt het Cybersecurity and Infrastructure Security Agency (CISA) van het Amerikaanse ministerie van Homeland Security. OFBiz ... Read more

-
The Cyber Express
Critical Apache OFBiz Vulnerability CVE-2024-38856 Identified and Actively Exploited
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has flagged a security vulnerability affecting Apache OFBiz, the open-source enterprise resource planning (ERP) system. This Apache OFB ... Read more

-
The Hacker News
CISA Flags Critical Apache OFBiz Flaw Amid Active Exploitation Reports
Software Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a critical security flaw affecting the Apache OFBiz open-source enterprise resource ... Read more
The following table lists the changes that have been made to the
CVE-2024-38856 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Oct. 23, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-38856 Types: Third Party Advisory, US Government Resource -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-38856 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-38856 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-38856 -
Modified Analysis by [email protected]
Dec. 20, 2024
Action Type Old Value New Value Changed CPE Configuration OR *cpe:2.3:a:apache:ofbiz:*:*:*:*:*:*:*:* versions up to (including) 18.12.15 OR *cpe:2.3:a:apache:ofbiz:*:*:*:*:*:*:*:* versions up to (excluding) 18.12.15 Changed Reference Type http://www.openwall.com/lists/oss-security/2024/08/04/1 No Types Assigned http://www.openwall.com/lists/oss-security/2024/08/04/1 Mailing List Changed Reference Type https://ofbiz.apache.org/security.html Vendor Advisory https://ofbiz.apache.org/security.html Patch -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Nov. 21, 2024
Action Type Old Value New Value Added Reference http://www.openwall.com/lists/oss-security/2024/08/04/1 -
Initial Analysis by [email protected]
Aug. 28, 2024
Action Type Old Value New Value Added CVSS V3.1 NIST AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Changed Reference Type https://issues.apache.org/jira/browse/OFBIZ-13128 No Types Assigned https://issues.apache.org/jira/browse/OFBIZ-13128 Issue Tracking Changed Reference Type https://lists.apache.org/thread/olxxjk6b13sl3wh9cmp0k2dscvp24l7w No Types Assigned https://lists.apache.org/thread/olxxjk6b13sl3wh9cmp0k2dscvp24l7w Mailing List, Vendor Advisory Changed Reference Type https://ofbiz.apache.org/download.html No Types Assigned https://ofbiz.apache.org/download.html Product Changed Reference Type https://ofbiz.apache.org/security.html No Types Assigned https://ofbiz.apache.org/security.html Vendor Advisory Added CPE Configuration OR *cpe:2.3:a:apache:ofbiz:*:*:*:*:*:*:*:* versions up to (including) 18.12.15 -
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
Aug. 28, 2024
Action Type Old Value New Value Added Vulnerability Name Apache OFBiz Incorrect Authorization Vulnerability Added Required Action Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable. Added Due Date 2024-09-17 Added Date Added 2024-08-27 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Aug. 06, 2024
Action Type Old Value New Value Added CVSS V3.1 CISA-ADP AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N -
CVE Received by [email protected]
Aug. 05, 2024
Action Type Old Value New Value Added Description Incorrect Authorization vulnerability in Apache OFBiz. This issue affects Apache OFBiz: through 18.12.14. Users are recommended to upgrade to version 18.12.15, which fixes the issue. Unauthenticated endpoints could allow execution of screen rendering code of screens if some preconditions are met (such as when the screen definitions don't explicitly check user's permissions because they rely on the configuration of their endpoints). Added Reference Apache Software Foundation https://ofbiz.apache.org/download.html [No types assigned] Added Reference Apache Software Foundation https://ofbiz.apache.org/security.html [No types assigned] Added Reference Apache Software Foundation https://lists.apache.org/thread/olxxjk6b13sl3wh9cmp0k2dscvp24l7w [No types assigned] Added Reference Apache Software Foundation https://issues.apache.org/jira/browse/OFBIZ-13128 [No types assigned] Added CWE Apache Software Foundation CWE-863